How to access your computer from anywhere using Chrome Remote Desktop
 Looking for a quick and easy way to access your Windows, Mac or Linux machine from an Apple device, an Android device or even from another Windows, Mac or Linux machine?
Looking for a quick and easy way to access your Windows, Mac or Linux machine from an Apple device, an Android device or even from another Windows, Mac or Linux machine?
If so, then there is one solution that works really, really well: Chrome Remote Desktop.
In order to use it, all you need is Google Chrome installed on your device.
After setting everything up, which we will explain below, you can access any of your computers from your device. This means you can remotely control your Windows machine from my iPhone, Nexus 6 and Mac laptop without having to worry about port forwarding, dynamic DNS, different operating systems or anything else.
The great advantage about using Google Chrome is that it takes about 5 minutes to setup and even less than that if you already have Chrome installed on your devices.
Install Chrome Remote Desktop
The first thing we need to do is install Google Chrome itself on your computers. Since Chrome can be installed on Windows, Mac or Linux, it means you can remotely access any of those systems too.
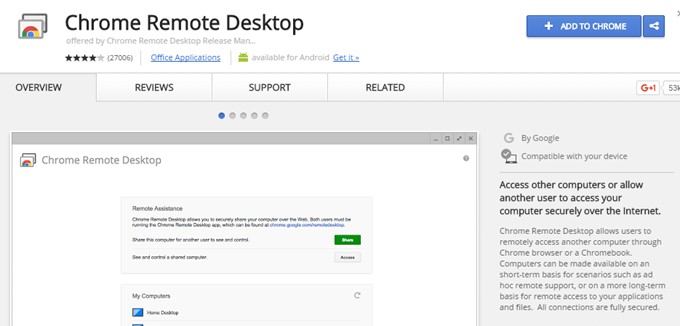
Once you have Chrome installed, you need to install the free Chrome Remote Desktop add-on. Click the Add To Chrome button at the very top right. A popup will appear with the permissions the app needs in order to work properly. Click Add App to continue if you’re OK with the permissions.
At this point, the app should be installed and a new tab should appear where you can see all the apps that have been installed in Chrome. If this tab doesn’t appear, just open a new tab and type in chrome://apps/ in the top address-bar.
Read more




 Not everyone is fortunate enough to have uncapped internet all the time. Have you ever wondered where your monthly internet bandwidth has gone to?
Not everyone is fortunate enough to have uncapped internet all the time. Have you ever wondered where your monthly internet bandwidth has gone to? 










