How can you encrypt sensitive files that are stored on a flash drive or external hard drive?
Flash drives are easy to lose. And anything lost can fall into the wrong hands. So if you’re carrying around sensitive information in your pocket, you need to make sure those files are encrypted.
Below are three easy solutions:
1. Buy an encrypted drive
You can buy a flash drive with built-in encryption, such as the DataTraveler Locker+ G3. When you plug the Locker+ in, it comes up as a 13MB, read-only drive. But once you launch the program file on that drive and enter the password that you previously setup, another drive opens up with all the storage space you paid for.
That drive, of course, is inaccessible without the password. The software runs off the drive, and it can be used on multiple computers and operating systems.
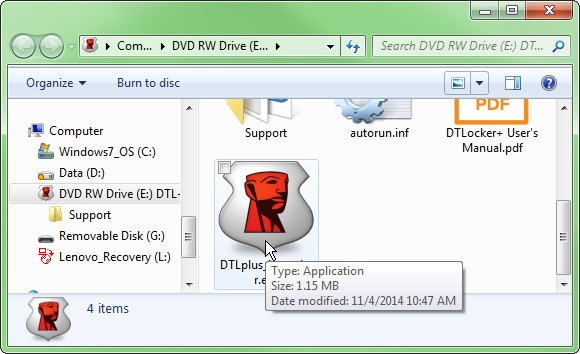
But I strongly recommend against using this drive’s optional cloud backup feature. It uses Dropbox, OneDrive, or whichever cloud service you pick, which at first glance seems like a nice convenience.

But this feature uploads the files without its own encryption. That means you’re trusting your sensitive files to the encryption capabilities of Dropbox and similar 3rd party services and you have no control over the encryption methods. Find another way to backup these files—preferably one where you can can control the encryption.
The DataTraveler Locker+ G3 starts at about $15 for the 8GB drive, and we've looked at other encrypted USB drives as well.
2. Install specialized software on your drive
Read more